Quantum Computing Cybersecurity: Risks & Strategies
- Işınsu Unaran
- May 6, 2025
- 4 min read
Quantum computing is no longer a distant concept. Major governments, tech giants, and startups are racing to develop machines that leverage quantum mechanics to solve problems traditional computers cannot.
While the benefits could revolutionize industries from materials science to logistics, the emergence of quantum computing also carries a heavy warning for cybersecurity. The cryptographic foundations that protect today’s data and systems could become vulnerable in a post-quantum world. Preparing for that future is no longer optional.
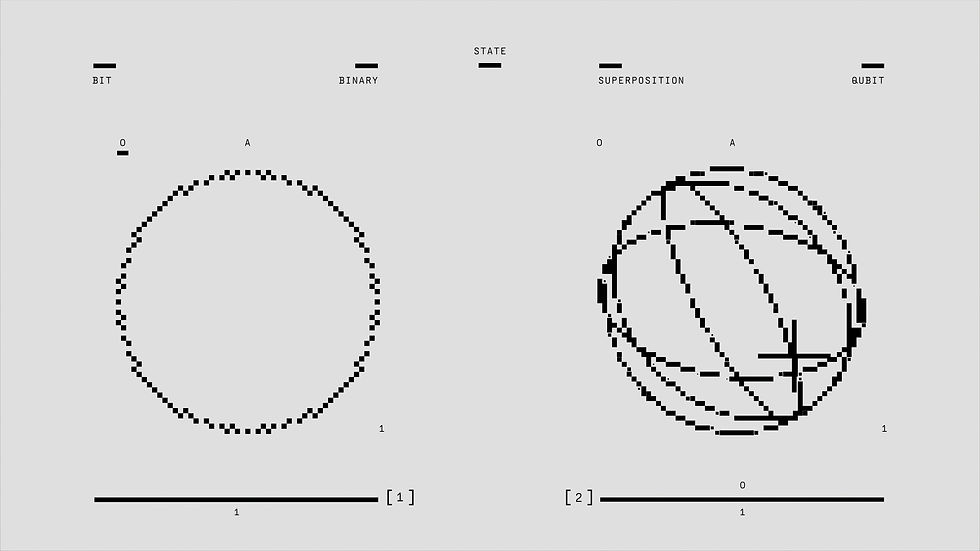
What is Quantum Computing?
Quantum computing represents a fundamental shift in how computation works. Instead of using classical bits, which exist as either 0 or 1, quantum computers use qubits, which can exist as 0, 1, or both simultaneously through a property called superposition. Qubits can also be entangled, meaning the state of one qubit directly relates to the state of another, even across distance.
These quantum properties allow quantum computers to perform certain calculations exponentially faster than classical computers. Problems that would take centuries to solve today could be cracked in hours. While still in the early stages of development, working quantum systems have already demonstrated the potential to disrupt fields dependent on complex computation, including cybersecurity.
Quantum Key Distribution (QKD)
Quantum Key Distribution (QKD) is often touted as a future-proof method for securing communication. Unlike classical key exchange methods, QKD uses quantum mechanics to distribute encryption keys securely. Any attempt to intercept or measure the qubits involved in the key distribution would disturb their quantum state, alerting both parties to a possible eavesdropper.
Protocols like BB84 (developed in 1984) form the basis of QKD, and practical QKD networks are already being piloted, particularly in sectors where national security is paramount. However, QKD is not a silver bullet. Implementing it globally presents significant challenges, such as distance limitations and the need for specialized infrastructure like quantum repeaters.

Quantum Cryptography (QC)
Quantum cryptography extends beyond QKD. It envisions a future where cryptographic systems are inherently quantum-safe, leveraging quantum mechanical principles to secure data and authenticate users. In theory, quantum cryptographic methods could resist both quantum and classical attacks.
However, most applications of quantum cryptography remain theoretical or highly experimental. In the immediate future, the more pressing issue is not building quantum cryptography, but rather defending existing classical systems against quantum threats.
Quantum Computing Cybersecurity Risks
The most significant cybersecurity threat quantum computing poses is its potential to break the cryptographic algorithms that secure the modern internet, financial systems, and critical infrastructure.
Quantum Decryption
At the heart of today’s secure communications are asymmetric encryption algorithms like RSA, ECC (Elliptic Curve Cryptography), and DH (Diffie-Hellman). These algorithms rely on mathematical problems that are easy to compute in one direction but practically impossible to reverse without a secret key, given today’s computational limits.
Quantum computers change that equation. Algorithms like Shor’s algorithm, developed in 1994, show that a sufficiently powerful quantum computer could efficiently factor large integers and compute discrete logarithms. In simple terms, this means that RSA and ECC could be broken in a fraction of the time it would take classical systems.
The implications are profound. Confidential emails, financial transactions, medical records, and state secrets—all encrypted today under assumptions of classical computational limits—could be retroactively decrypted once powerful quantum machines become operational. This looming threat is often referred to as “harvest now, decrypt later,” where attackers collect encrypted data now with the intention of decrypting it once quantum computing becomes viable.
Symmetric cryptographic algorithms, such as AES, are more resistant but not immune. Quantum algorithms like Grover’s algorithm can speed up brute-force attacks against symmetric encryption, effectively halving their security strength. This means that AES-256, for example, would offer roughly the equivalent security of AES-128 in a quantum context.
Strategies for Post-Quantum Cybersecurity
Organizations must prepare now for a post-quantum world. Transitioning to quantum-safe methods will require careful planning, because cryptographic infrastructure underpins virtually every digital system.
Post-Quantum Cryptography
Post-Quantum Cryptography (PQC) refers to cryptographic algorithms designed to be secure against both quantum and classical computers. Unlike QKD, PQC does not require quantum infrastructure. It can run on existing systems but uses mathematical problems that quantum computers cannot efficiently solve.
In 2016, the U.S. National Institute of Standards and Technology (NIST) launched a competition to standardize post-quantum cryptographic algorithms. After several rounds of evaluation, finalists have been selected for algorithms such as CRYSTALS-Kyber (for key encapsulation) and CRYSTALS-Dilithium (for digital signatures).
Migration to PQC is complex. Systems must first inventory where cryptography is used, not just in communication channels but also in databases, firmware, authentication systems, and backup archives. Implementing hybrid models that combine classical and quantum-safe algorithms is a recommended intermediate step to ensure backward compatibility while future-proofing security.
Beyond PQC, other strategies include increasing symmetric key lengths, improving key management practices, and deploying quantum-resistant secure messaging protocols.

The Urgency of Quantum-Ready Cybersecurity
While functional, large-scale quantum computers capable of breaking RSA or ECC are still years away, the window to act is short. Given the complexity and sheer scale of the systems involved, the migration of global infrastructure toward quantum-resistant models will take a decade or more.
Enterprises and governments that wait until quantum threats materialize will be too late. Data harvested today—financial transactions, healthcare data, intellectual property, classified government communications—could be decrypted later. The risk is cumulative.
Quantum computing will deliver extraordinary benefits to humanity. But without a proactive approach to cybersecurity, it could also open the door to catastrophic breaches. Recognizing this double-edged sword and acting now is critical.
Quantum-safe cryptography is not just an engineering challenge; it is a strategic imperative for national security, financial stability, and trust in the digital economy.
At DataFlowX, we recognize that future cybersecurity challenges require an architecture that assumes evolving threat landscapes, not static ones. Our solutions are designed around Zero Trust principles, hardened isolation, and proactive threat detection to defend sensitive data even against unknown or emerging threats like those posed by quantum computing. While quantum risks target cryptographic foundations, the need for robust segmentation, data diode-based unidirectional data flows, and deep content inspection remains universal.
Preparing today’s infrastructure for tomorrow’s adversaries is at the core of how DataFlowX builds resilience into every layer of cybersecurity.









